Top Security Threats and Security Analysis Tools for Front-end Developers
- Chetan Chaand
- April 22, 2020
- 7 Minute Read

That’s not how you’d want to protect your estate, right? You’d want a fence to go with that gate.

In the digital domain, that translates to keeping your website and online data secure and protected from unauthorized access.
Websites have a front-end and a back-end. They need different security tools. When you hire front-end developers they should be well-versed with these tools. This post focuses on the top security analysis tools that front-end developers must know about and apply.
Two Levels of Front-end Security
The front-end of a website is the part that your visitors and clients interact with. Even then, there are two dimensions to front-end security :
Keeping Your Clients’ Data Safe
This in itself is a vast topic. A lot of your customers’ personal data will be on your website. It is part of your responsibility to protect such information from leakage or hacking.
Keeping Your Own Data Safe
You need to prevent customers/visitors to your website from accessing your own data that they do not need to see. This is where front-end-security meshes with back-end security.
The first step for both is to detect the security threats that your front-end may be exposed to.
Top 10 Threats to the Safety of Your Clients’ Data
We briefly describe the security threats from the OWASP (Open Web Application Security Project) Top 10 list. These threats represent a global consensus on the most critical and common front-end vulnerabilities.
Threat 1. SQL Injection Attacks
SQL vulnerability is one of the most prevalent security threats. Many high-level data scams in recent times have been carried out using SQL injections. It is a code injection technique used to conduct attacks against data-dependent applications.
SQL injection is the technique by which an attacker manages to interfere with the questions the app sends to its database. That is how they gain access to unauthorized data.
A 2017 post says that hackers use this method in 51% of their attacks.
Threat 2. Broken Authentication
Incorrect implementation of authentication and session management is a serious threat. That allows cyber-criminals to compromise keys, passwords, or session tokens. It may facilitate an attacker to impersonate other users for a while or forever.
A 2019 vulnerability assessment report says 9 out of 10 web applications are vulnerable to hacking attacks. The application code is the location of 82% of the threats.
We invite you to consider the following graph carefully.
A 2019 vulnerability assessment report says
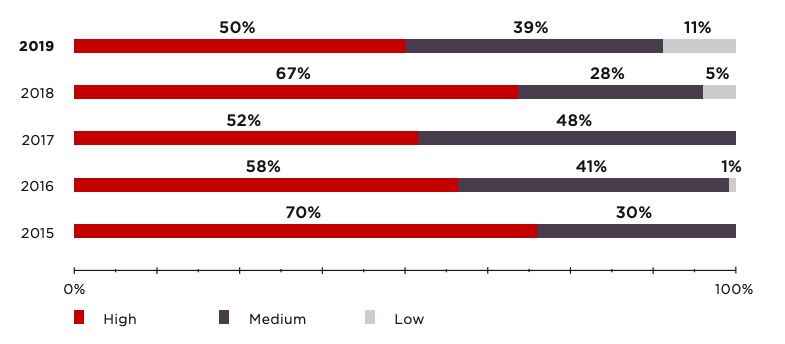
Notice that there has been a considerable reduction in high-level and low-level threats from 2018 to 2019. Medium-level threats have increased, however.
Now notice the whole graph carefully once more. High-risk threats were high in 2015 and then reduced over the next two years. They shot up again in 2018 and reduced in 2019.
There’s a clear pattern.
- As protection mechanisms improve, cyber-criminals find newer ways of attacking.
- When high-level threats decrease, mid-level threats rise,
These are important points to remember when you decide which threat analysis tool you want to use.
Threat 3. Sensitive Data Exposure
Sensitive data needs special protection like encryption during rest or transit. Exchanging such data with the browser needs special precautions. Web applications and APIs sometimes do not code such special protections. That enables credit card fraud, identity theft, and similar other serious cyber-crimes.
Threat 4. XML External Entities (XXE) Injection
This allows an attacker to interfere with the way an application processes XML data. It happens because of older versions of XML. Also due to poor configuration. XXE facilitates the attacker’s access to the app’s server file-system.
The attacker can interact with any back-end systems or external systems accessible to the app. This vulnerability includes disclosure of internal files, internal file shares, remote code execution, etc.
It is also possible to leverage XXE vulnerability to execute Denial of Service (DOS) attacks, or Server-Side Request Forgery (SSRF).
Threat 5. Broken Access Control
Poor enforcement of what authenticated users can and cannot do is a vulnerability. Cyber-criminals can use such gaps to gain unauthorized access to data and/or functionality. The results can be dangerous as it allows the attacker to change other users’ data, modify access rights, or even delete crucial data.
Threat 6. Security Misconfiguration
This is one of the most prevalent vulnerabilities. Ad hoc or incomplete configurations, insecure default configurations, misconfigured HTTP headers, and open cloud storage are the typical examples.
Wordy error messages also contain sensitive information sometimes. Irregular patching/upgrading is another instance of security misconfiguration.
Threat 7. Cross-site Scripting (XSS)
This is a vulnerability of web applications that allows an attacker to bypass access controls like the same-origin policy. The attacker can vandalize websites, or redirect the user to malicious sites, etc. It also facilitates injecting malicious elements in a benign or trusted website.
Threat 8. Insecure Deserialization
This weakness can cause remote code execution as it allows the attacker’s data to be accepted without verification. Data theft, data modification, injection attacks, privilege escalation attacks, replay attacks, etc, can all happen because of this lapse.
Threat 9. Using Components Known to be Vulnerable
Using components that are known to be vulnerable weakens the defense of an application. That can lead to attacks ranging from data loss to server hijacking.
Threat 10. Inadequate Logging and Monitoring
This gap allows cyber-criminals to continue attacking systems persistently over a period of time. That creates a scope to access more systems and destroy, mess up, or steal huge amounts of data.
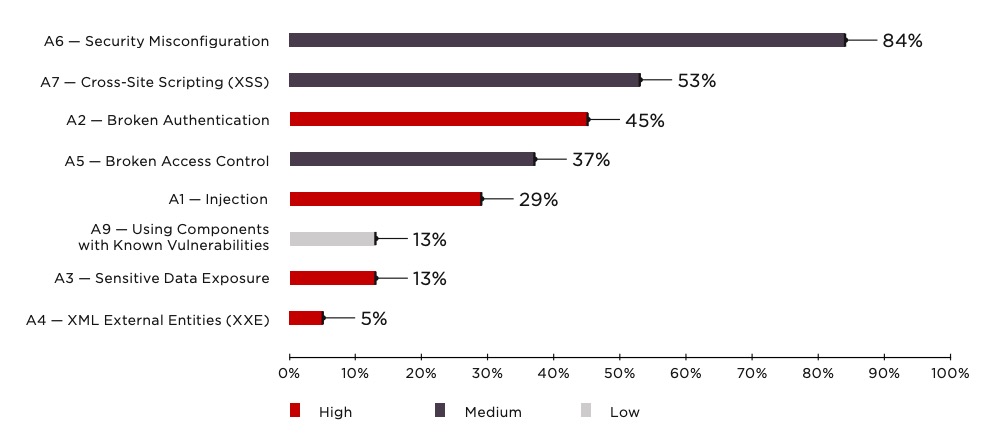
How the Threats Compare
The graph below reflects clearly the relative prevalence of 10 threats we have described above.
The Top 7 Free Security Analysis Tools
Now that you know the most prevalent vulnerabilities, you need to detect if your system is vulnerable to any or all of these. This is where front-end security analysis tools come in.
There are both open-source and commercial tools in the market to analyze security threats. We have selected the best from the free tools only. In-depth research, including user reviews, constitute the basis of our selection.
We have included tools that can detect the top 10 vulnerabilities we have described, ala OWASP.
Just one word of caution before we begin. Security testing needs to be a part of the website development process – not an afterthought.
Tool 1. OWASP ZAP
OWASP Zed Attack Proxy. That’s the full name of ZAP. It is one of the most popular and widely used security analysis tools. Companies like Google and Microsoft use it.
Pros
- Free to download and easy to use, it supports both manual and automated testing.
- Platforms like Linux, Mac OS, and Windows support it. It comes with a wide variety of features that enable efficient penetration testing.
- Strong community support is another advantage of ZAP. Also, updates including new vulnerabilities are consistently regular.
- You can use a number of plugins and integration with tools like Jenkins considerably heightens ZAP capability.
Cons
- According to users, the only area of improvement for ZAP is its reporting. Its reports are not as comprehensive as its security scans.
Tool 2. Arachni
Arachni is another open-source and popular security testing tool with a powerful Ruby platform. It also works for Linus, Mac OS, and Windows.
Pros
- As a fully automated system, Arachni works fast.
- Its penetrative testing capacity is quite comprehensive.
- Modularity and scalability are the two most celebrated features of this tool.
- It is also quite user-friendly and offers a support portal. The resources available there are substantive.
- You can add a whole range of plugins for extra functionality.
Cons
- Works only on the base URL – you cannot scan a particular directory.
- It doesn’t offer a scanning profile.
- Arachni’s community support can improve.
Tool 3. Acunetix
Another fully automated open-source vulnerability scanner with considerable popularity. Acunetix has a commercial version also, but the user rating for the free version is fairly high.
Acunetix has three paid plans: Standard, Premium, and Acunetix 360. The company website does not offer any fixed price range for any of the plans. The practice seems to be of variable pricing.
You have to key in the number of websites you want to be scanned. Only then you can get the price.
Pros
- It is easy to use.
- The company offers good support.
- The paid versions give you in-depth reports to help you where exactly you need to strengthen your website’s security.
- The paid versions offer lots of tools to use.
Cons
- Some feel it is over-protective and also scans what it need not.
- Some users have complained that updates are slow to release.
- The free version does not describe the causes of the vulnerabilities.
Tool 4. SonarQube
This open-source security analysis tool is a useful one to measure the strength of the source code. SonarQube is particularly efficient in identifying tricky issues.
Its Community Edition is free to use. There are three paid plans also. The Developer Edition starts at €120. The Enterprise Edition has a starting price of €15,000. For the Datacentre Edition, the starting price is €100,000.
Pros
- It is written in Java, but it can read 20 different languages.
- Easy integration with tools like Jenkins.
- It allows a wide range of customization.
- In-depth analysis reports with estimated time-to-fix.
Cons
- IDE and SonarQube are not compatible.
- There is scope to improve integration with Jira and GitHub.
- The support forum for the open-source version is weak. Lines of Code – Starts at €12
Tool 5. Grabber
Grabber is a portable and free security tester that has a good capacity in detecting security threats. It’s written completely in Python. However, it is good only for small web applications.
Pros
- Easy to use with simple command lines.
- Allows extension of the attack list.
- It generates a live and interactive HTML report.
Cons
- No Graphic User Interface (GUI)
- It becomes slow when applied to large applications with considerable amounts of data.
Tool 6: Burp Suite
Burp Suite is a set of software security tools that is largely used for penetration testing of web applications. Within the tool repository of Burp Suite some of the popular choices are Proxy, Spider, Repeater, Intruder, Sequencer, and many more.
Let’s look at some of the pros and cons of implementing this security analysis tool.
Pros:
- It’s suitable for beginners as well as intermediates being a highly extensible and feature-rich tool.
- There is a free community edition as well as a paid professional edition with advanced features and functionalities.
- There is a detailed report available with a user-friendly interface.
Cons:
- The paid edition is considerably expensive.
- It can be complicated for beginners to set up and use it effectively.
Tool 7: W3af (Web Application Attack and Audit Framework)
This framework deals with auditing the attacks and vulnerabilities of web applications. It has been developed using Python and it offers customized HTTP requests to identify issues in the web application.
Pros:
- Open-source and actively developed.
- There are a variety of plugins for vulnerability scanning.
- Availability of Command-line and GUI interfaces.
Cons:
- The usage of this interface can be complex for those who are freshers in the web security testing segment.
- All modern web application vulnerabilities might not be covered in the tool.
Top Priority
Be alert to evolving security threats and take steps to keep your own data safe from attacks. Strengthen your back-end and design your front-end to respond to back-end security.

Thank you for submitting the details!
We will keep your information safe. Feel free to contact us with any questions at hello@uplers.com
Please check your email for next steps shared by Robert.